As a veteran, you’ve already proven your ability to adapt, learn quickly, and handle challenging environments. Now, you’re considering transitioning into a new field—technology. You may feel overwhelmed, uncertain where to start, or even unsure if the tech industry is the right fit for you. Let me assure you, the skills you’ve developed in the military are more transferable than you think, and the tech industry is an excellent place to leverage them.
In this post, we’ll break down how to transition into tech as a veteran, what makes the tech field a great fit, and how you can make your move effectively and efficiently. Whether you’re aiming for cybersecurity, software development, data analysis, or any other role in tech, this guide is designed to help you succeed.
1. Identifying Transferable Skills
One of the first things to recognize is that your military experience has already equipped you with a set of skills that are highly valuable in tech. Problem-solving, teamwork, leadership, and attention to detail are just a few. Whether you were troubleshooting equipment, managing personnel, or analyzing complex situations, you’ve gained experience that’s applicable in the tech world.
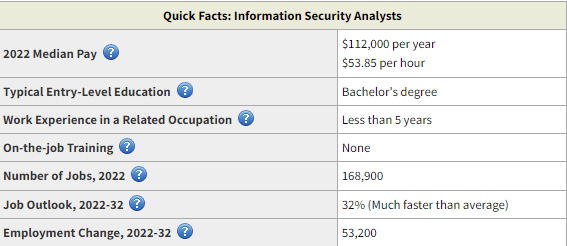
If you’re considering cybersecurity, for example, your experience handling classified information or working with security protocols directly aligns with many roles in that field. Understanding how to apply those experiences to your tech career is key to standing out as a strong candidate.
2. Researching Tech Roles That Fit Your Interests
The tech industry is vast, and there are many paths you can take. But to make your transition smoother, it’s crucial to identify specific fields that match both your interests and your strengths. Are you drawn to defending systems from cyber threats? Cybersecurity could be your path. Enjoy breaking down data? Data analysis might be a good fit. Maybe you like problem-solving through code—software engineering may be your calling.
Spend time researching various roles to see which ones resonate with you. There are many online resources available (which we’ll list at the end) that provide detailed overviews of what each tech career entails.
3. Seeking Education and Certification
Veterans often have access to GI Bill benefits that can cover education and training in tech. There are countless certification programs, online courses, and bootcamps tailored to veterans who are transitioning into tech.
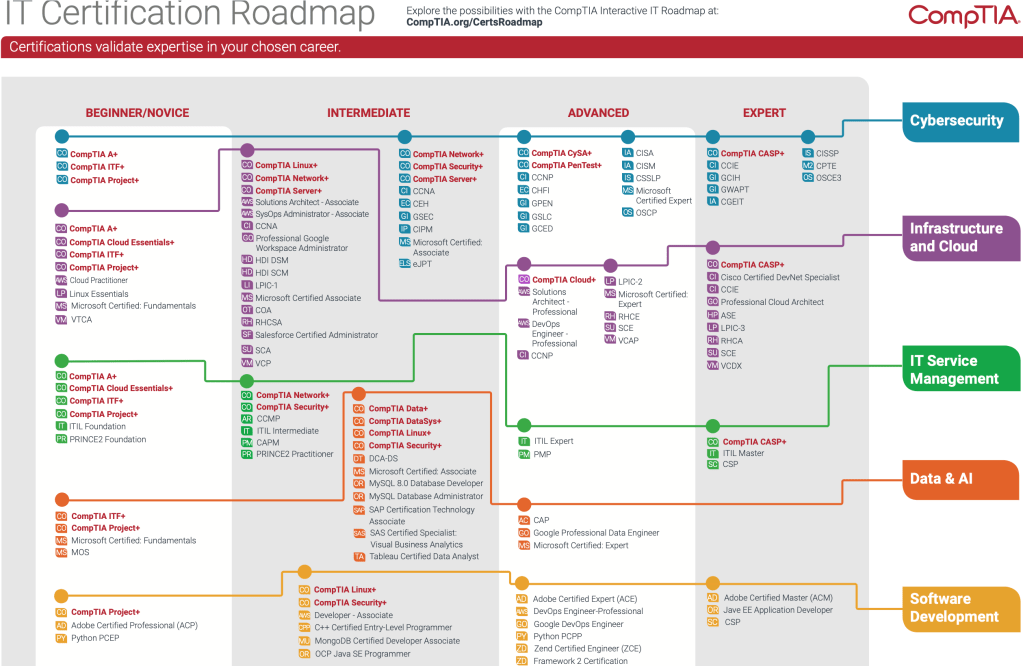
Some popular certifications to consider include:
- CompTIA A+ for IT fundamentals
- CompTIA Security+ for cybersecurity basics
- AWS Certified Cloud Practitioner for cloud computing
- Certified Ethical Hacker (CEH) if you’re interested in penetration testing
Leverage these programs to build your knowledge and show employers that you’re serious about your new career. Many tech companies look for certifications as proof of a candidate’s readiness for a role.
4. Networking: Building Connections in Tech
One thing that’s often overlooked in a career transition is the importance of networking. Your military network is strong, but now it’s time to start building your tech network. Start connecting with people on LinkedIn who are already working in the industry. Attend tech meetups, webinars, and online events where you can meet professionals and learn more about the field. Many veterans have successfully transitioned to tech, and they can provide valuable advice and mentorship.
Consider joining veteran-specific tech organizations and programs. Organizations like Vets in Tech and Operation Code provide resources, training, and mentorship to help veterans break into the tech industry.
5. Transition Programs for Veterans
There are several programs specifically designed to help veterans transition into tech careers. For instance:
- DoD SkillBridge: A program that connects service members to internships and training programs with tech companies during their last 180 days of service.
- Onward to Opportunity (O2O): A career training program that offers free tech certifications to veterans and military spouses.
- Veterans Employment Through Technology Education Courses (VET TEC): A VA program that covers the cost of training programs in high-demand tech fields.
These programs provide a direct pathway to the skills, certifications, and networking opportunities you need to start a successful tech career.
Conclusion:
Transitioning into the tech industry as a veteran can feel like a daunting challenge, but it doesn’t have to be. The key is recognizing the value of the skills you’ve already gained in the military, researching the tech fields that align with your interests, and leveraging the many resources available to help veterans make the shift. With dedication, education, and the right connections, you can build a fulfilling, high-paying career in tech.
As you explore this journey, remember that the tech industry needs people with your unique perspective, discipline, and experience. The opportunities are out there—you just need to take the first step and commit to the process.
Resources for Veterans Transitioning into Tech:
- Vets in Tech: https://vetsintech.co
A community that supports veterans through tech education, entrepreneurship, and employment opportunities. - DoD SkillBridge: https://dodskillbridge.usalearning.gov
A program offering internships and job training in the tech sector for transitioning service members. - Onward to Opportunity (O2O): https://onward2opportunity.org
Provides free tech training and certifications for veterans and military families. - Operation Code: https://operationcode.org
A nonprofit that helps veterans learn to code and land software development jobs. - Veterans Employment Through Technology Education Courses (VET TEC): https://www.va.gov/education/about-gi-bill-benefits/how-to-use-benefits/vet-tec
A VA program offering training in tech fields with GI Bill benefits. - LinkedIn for Veterans: https://linkedin.com/military
Free premium LinkedIn membership for veterans to build their professional network. - VA Certification Reimbursement Program: Veterans can take advantage of the VA’s Certification Reimbursement Program, which reimburses the cost of certification exams, making it easier to achieve necessary credentials without financial strain. Learn more about how to use your GI Bill benefits for certification and test fees here: VA CertificationReimbursement Program.